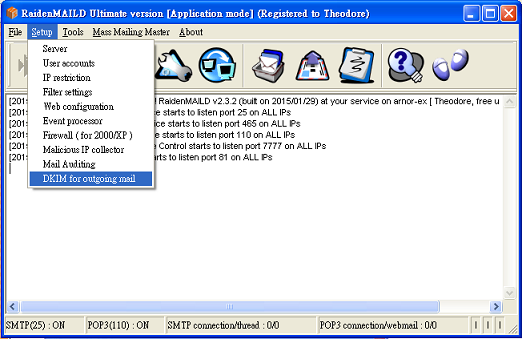
After version 2.3 , RaidenMAILD adds DKIM for outgoing mail. It could sign your outgoing mail with DKIM signature. If you need to know more detail about DKIM, please refer http://en.wikipedia.org/wiki/DomainKeys_Identified_Mail
To use DKIM, you need two important settings as following. Take mail-server.tw as domain example, we need to specify a selector string to recognize the key pair which server uses. In this example, we use s1024 as selector of mail-server.tw.
- Mail Server side: We need to generate a keypair first (private key file and public key file) and set s1024 to be selector for mail-server.tw to enable DKIM for the domain.
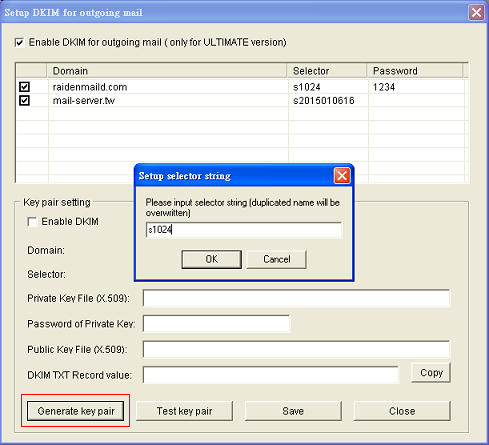
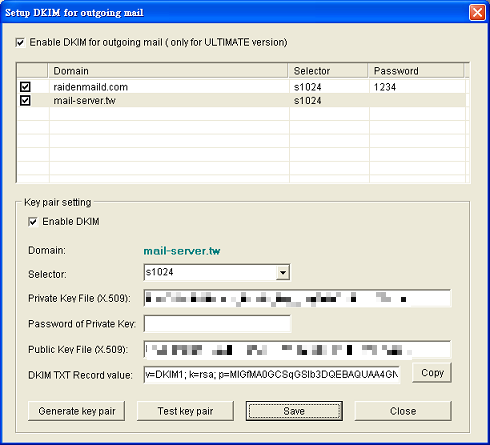
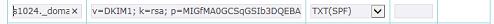
- DNS Server side: In DNS Server, we need to create a TXT record named s1024._domainkey.mail-server.tw , The text content of the record is the DKIM TXT RECORD when you done key pair generating. The contents looks like below:
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDKhp5D
aXKuJM9wV6Ta2/ywdAsOKLBqL71Wb6nx5q0QRDVQrBhemMiMwzj1fXsBGKn43ojZ
zfNCjThVTrgJ31pCwzTWLQy5zIzXSUaI179Z8OgKyVf7IYsw6XcmryI040k4Jrt5OX03
bw7m0bfhDOKxIBHD7BXCScGRIiuBB+n0PwIDAQAB
(Ignore the Carriage-Returnn, above is a continuous string)
After finishing these two settings, you need to wait the TXT record to take effect.
How to test DKIM? First, I want to show you how to use nslookup command to query DKIM TXT Record.
C:\nslookup
> set q=txt
> s1024._domainkey.mail-server.tw
Server: hntp1.hinet.net
Address: 2001:b000:168::1
Non-authoritative answer:
s1024._domainkey.mail-server.tw text =
"v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDKhp5D
aXKuJM9wV6Ta2/ywdAsOKLBqL71Wb6nx5q0QRDVQrBhemMiMwzj1fXsBGKn43ojZ
zfNCjThVTrgJ31pCwzTWLQy5zIzXSUaI179Z8OgKyVf7IYsw6XcmryI040k4Jrt5OX0
3bw7m0bfhDOKxIBHD7BXCScGRIiuBB+n0PwIDAQAB"
>
If the record is successfully queried, it means your DKIM is ready to go. Send a mail from @mail-server.tw to yahoo/gmail...etc, then find your mail and check the mail source/header, you may find the following information in mail headers.
Authentication-Results: mta1067.mail.tw1.yahoo.com from=mail-server.tw; domainkeys=neutral (no sig); from=mail-server.tw; dkim=pass (ok)
This means your mail was successfully added DKIM signature to it and passed the DKIM checking.
One more thing needs to be clear. A DKIM mail doesn't mean it will not be treated as spam mail, it is just a mechanism to identify the mail host which sent from. |



